In this post we’re going to start by talking about how a VPN, Tor Network and Apple iCloud Private Relay works, and then we’re going to discuss what their differences are and when they can become useful.
A small and boring disclaimer before we start. All the ‘illegal activities’ I’m going to refer to in this post are not necessarily illegal as you can imagine (e.g. buying guns/drugs), they could also be illegal for a specific government (e.g. activism against your government).
Government outlaw activities which can be perfectly moral. Laws can be immoral laws, even when they pretend to encode morality.
Let’s start by explaining the basics for being able to fully understand the role of the tools that we’re going to dive into later: we will just talk about personal usage and not about corporate usage (e.g. Site-to-site VPN).
When we search for a website, our request goes through a DNS Server (usually of our ISP-provider) that is going to resolve the request and return the corresponding IP address. As you can image, by doing that our ISP or a third party public DNS server (e.g. Google) is able to collect all website we visited (they are forced to do this logging by law in some countries) and in case of investigations cooperate with law enforcement or sell them to a third party (not in EU thanks to GDPR, where they would need to have your explicit consent in order to sell your traffic data).
IP address are often used together with cookies to build a profile of our behaviour and for example register how many times we are visiting a certain page of a website, for example Pixel snipped from Meta that retrieve data from HTTP header. Data Brokers can collect single pieces of our information and aggregate them together thanks to the same IP address, email or other personal information, having a clear idea of what a user likes and what he is searching for.
VPN - Virtual Private Network
What a VPN does is create an encrypted connection to the VPN company’s DNS Server instead of your default one and make requests to the websites on their behalf.
Before we continue, we need to understand that by using a VPN we’re just changing who can see our data ISP → VPN provider; all our requests are going to pass through VPN company’s servers creating a single point of failure. A key mantra to remember is that:
VPNs are honeypots
Using a VPN will just give you better privacy in certain situations, it will not make you completely anonymous. A VPN is not a tool for illegal activities so don’t rely on a “no log” policy.
In some countries VPN companies are not obliged by law to collect logs, unlike internet service providers and a lot of them state that they have a ‘ZERO log’/‘no log’ policy, which is an ambiguous definition, usually some logs are kept during a session for maintenance and troubleshooting and depending on the company deleted after a period of time. The VPN service itself might be trustworthy, but they could use third-party services (payment processors, analytics) that log user data beyond the VPN provider’s control.
VPN encryption Protocols
- OpenVPN
OpenVPN it’s open source, highly configurable and employs various cipher suites (e.g. AES), for data confidentiality and integrity.
It uses the OpenSSL library, an implementation of SSL/TLS protocols, to facilitate the creation of encrypted tunnels. It supports both UDP and TCP transport protocols, offering flexibility. - WireGuard
WireGuard is a modern, easy to implement, VPN protocol designed with performance at its core, aiming to offer better performance than other protocols (generally faster than OpenVPN). WireGuard utilises ChaCha20 for encryption and Poly1305 for message authentication, but relies exclusively on UDP for transport, emphasising speed over potential reliability concerns in some network scenarios. - IKEv2/IPSec
Internet Key Exchange v2 used in combination with IPSec is a widely used protocol.
IKEv2 handles the authentication and establishment of an encrypted tunnel while IPSec employs algorithms like AES and SHA for data encryption and integrity checks, this combination offers high security with added benefits like mobility and multihoming support (MOM), making it particularly well-suited for scenarios where continuous transitions between networks are important (e.g. Wi-Fi to cellular). - Others
SSTP, L2TP/IPSec, SoftEther
Why should I use a VPN?
- Privacy
Your ISP (Internet Service Provider) cannot log your traffic and third-party actors are not able to get your original IP address. Apart from the average user, VPNs are essential tools for activists, journalists, and anyone who wishes to express dissent or expose government wrongdoing in countries with repressive regimes.
For example Russia plans to block VPNs because they “provides access to sites banned in Russia”; or China, with the “Great Firewalls” (GFW) that actively works to limit access to foreign information sources and actively works to block VPNs.
VPN blocking is usually done by deep packet inspection, IP blacklisting or port blocking. On the other hand, VPN services are trying to mask VPN traffic to make it look like regular web traffic and frequently switching server IP addresses to avoid blacklists. With this scope of usage an important feature to check before using a VPN is the VPN kill switch, which is a safety feature that automatically disconnects your device from the internet if your VPN connection drops out, preventing third parties from getting your IP or you from continuing to use the internet without knowing that you’re no longer protected by the VPN. - Change location
VPN companies have hundreds of different servers in different locations and that allows you to seem like you are located in the same country or region as the VPN server you choose. This can be useful for being able to access geo-restricted content, but usually, doing that violates the terms of service of the company. - Non-encrypted connections
Let’s start by saying that in 2024 more than 85% of all the public websites are using HTTPS and, as Google reports, around 96% of traffic across Google is made with HTTPS requests. This second percentage is higher for two main reasons: Google SEO gives a higher ranking to HTTPS websites, so there is a higher probability to visit them, and probably a large portion of all the traffic is from big websites that have HTTPS enabled. Visiting a non-encrypted website is very, very unlikely and with almost every browser when you enter one of them you receive an alert. In this scenario a VPN could be useful just if you have to enter data into a form and send them, thanks to the encrypted tunnel that it creates.
Why should I NOT use a VPN?
- Speed reduction and human checks
Using a VPN will add latency and reduce internet speed, that’s for three main reasons: distance between you and the VPN Server (usually worse than your default one), encryption algorithm used and server overload. Another element that can let your experience worst is that, VPNs server’s IP are used from thousand of people, so Google and other services can detect your IP as a suspicious one, and they’re going to check if you’re a real human asking you to solve boring puzzles or select fire hydrant images (e.g. CAPTCHA). - Malware protection and Data protection from “hackers”
Some companies (e.g.SOUTHVPN) state in some of their ads ‘thanks to our VPN all malware will be blocked’ or that if you’re using a VPN your data is not vulnerable. If the second statement ‘can be true’ in some rare condition that we analysed before, the first statement is completely false. A VPN does not stop any type of infected download or phishing attack, as we said before, it just encrypts outbound packets, it does NOT analyse or detect malware inside inbound packets in any way. - Because it’s free
VPNs companies are NOT non-profit organisations, as we stated at the beginning of the article, VPNs are honeypots and they “could” collect all the traffic that passes through them. Having servers is expensive so they have to make money somehow; many of them collect and sell browsing data and personal information to advertisers or third parties, completely defeating the purpose of a VPN meant for privacy protection. Some may even inject tracking code into your web browser or redirect your traffic for their own monetisation purposes. As you can understand, using a free VPN is not a good idea if you don’t want to make a big gift with a lot of your information inside to someone you don’t know. - If you’re already using DNS over HTTPS and DNS over TLS you don’t need it because you’re already asking a trusted third party company to resolve DNS queries, so your ISP cannot see this, can only see what IP address you’re connecting to.
VPN chaining
VPN chaining is the practice of connecting to multiple VPN servers in a sequence. In most cases this practice is not going to enhance your privacy and is probably going to just make your performance worse. It gives you near the same anonymity that you would get with Tor but likely paying more for your VPNs compared to TOR’s free access.
If you’re trying to keep a government from tracking you down, multiple VPNs again won’t gain you anything.
The government just needs to identify the last one in the chain, and then ask who’s paying for it. Here, TOR is better, since there’s no financial link to you.
What VPN should you use?
There’s this very well made article on questions you should ask before deciding which VPN to use.
Let’s see and discuss some of them:
- Who owns the VPN service?
It can be an useful information to deeply understand where your information is going, and if the VPN company is part of another bigger company group and if it has data related business or had security problems in the past. An example could be SurfShark, a famous VPN company that from February 2022 merged with NordSecurity (NordVPN) and was ‘created’ by the same startup accelerator (Tesonet) that owns and founded NordVPN company.
Another example can be made talking about VPN review websites, for example vpnMentor.com is owned by the same company that owns ExpressVPN and CyberGhost which of course are in the top 3 best VPN services. - What’s the business model behind the VPN service?
As we said before VPN companies are businesses, and for that reason they have to make money. If a VPN is free the money in 99.9% of the cases is made from your personal data, but you have to be aware that some companies that charge for their services could also sell your data to third parties (e.g. data brokers). - How does your VPN service handle inquiries from governments?
The best way to answer this question is looking for episodes that happened in the past and analyse how the VPN company handled the situation. This point is quite hard to generalise because the legislation can be quite different from country to country.
In conclusion, if you still think you want to subscribe to a VPN service, I suggest (no affiliate/adv):
- Mullvad
The company has a firm policy of not collecting user data and benefits from Sweden’s strong privacy laws. Mullvad maintains that if they were ever legally forced to collect data, they would rather shut down the service in that location than compromise their users’ privacy.
The Swedish police raided Mullvad’s office in Gothenburg, but did not take any customer data, likely due to the company’s policy of not retaining user information. - Proton VPN
ProtonVPN is another company that until today seems committed to transparency, ethics, and security. All ProtonVPN apps are open source and have been audited by third parties multiple times. They also provide a free version with just few server locations and quite slow speed. If I have to recommend one free VPN service, this one is probably the only one. Anonymous cryptocurrency and cash payment are accepted.
Apple Private Relay
iCloud Private Relay is a service released by June in 2021, included with an iCloud subscription. It works by routing your traffic through two separate internet relays (proxy servers). The first relay is the “Ingress proxy”, owned by Apple, that knows your IP, the second one is the “Egress proxy”, owned by a third-party content provider, that knows the website we’re trying to access but doesn’t know our IP.
Ingress proxy gives you back a General area (character representation of a specific geographic location) that you’re going to pass to the egress proxy that is going to use it to pick a new IP from a pool without knowing your original one, but maintaining a connection with your original IP location thanks to the general area information.
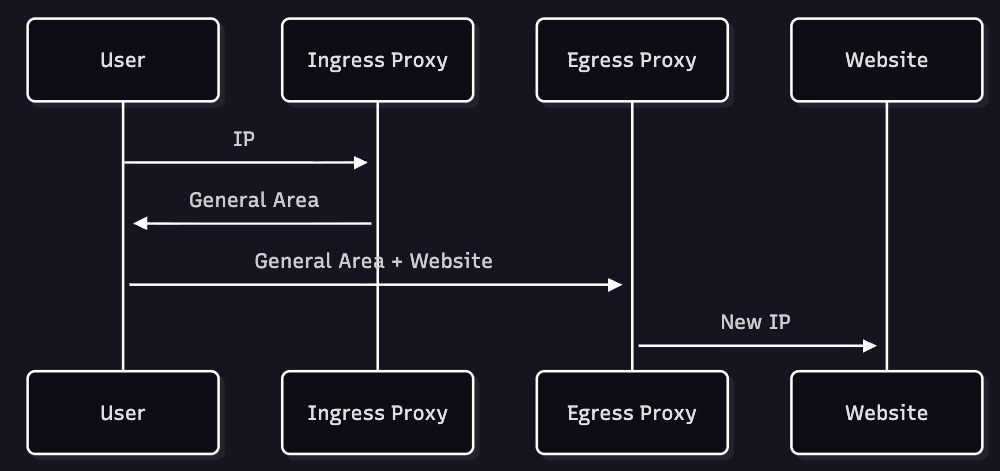
Private Relay manages network access without needing identity or account details, using RSA Blinded Signatures; A Private Relay Access Token Server provides your device a variety of tokens in advance, offering the flexibility to connect to any proxy operator whenever necessary without having to make a new request. It uses the concept of onion encryption but we’re going to talk about it more in the Tor chapter.
The protocol used is QUIC (Quick UDP Internet Connections) on port 443 and TLS 1.3 (built in it).
As Apple states, most partner providers annotate the IP addresses’ Organization field as “iCloud Private Relay”, so websites can recognise and not block them on their servers.
This could be a security issue for the companies that are going to whitelist these IPs, because in case someone gains access to one of the servers, they can potentially make any number of requests without being blocked by the firewall.
To prevent CAPTCHAs blocking traffic websites can use Private Access Tokens, which provide an alternative to verify a device and protect the server without slowing the user experience.
You cannot change the location of the ‘egress proxy’, as we said before, iCloud Private Relay tries to preserve the area the user is located in. Over time, the IP address chosen from the egress proxy is changed to prevent correlation from your researches to the same IP.
Privacy concerns
There is just one big problem about this service: it’s not open source.
It’s impossible for independent security researchers to scrutinise its implementation, they need to analyse it as a black box.
This lack of transparency could mean hidden vulnerabilities or potential backdoors that could compromise the privacy and security features it is supposed to provide.
Apart from that, the advantages of this service are that it does not create a single point of failure like a VPN, if Apple maintains the statement of two different providers for the nodes.
It’s also faster and more usable, than Tor, but less secure because it uses just two nodes.
Tor (The Onion Router) Network
Tor Network stands for ‘The Onion Router’ Network and it is an open source project that takes the privacy topic one step above the previous one.
With Tor we can access two types of websites:
- Clearnet services: websites that are in the ‘surface web’ and are accessible with any common browser
- Onion services: websites that can only be accessed over Tor and have additional privacy benefits that we’re going to discuss later
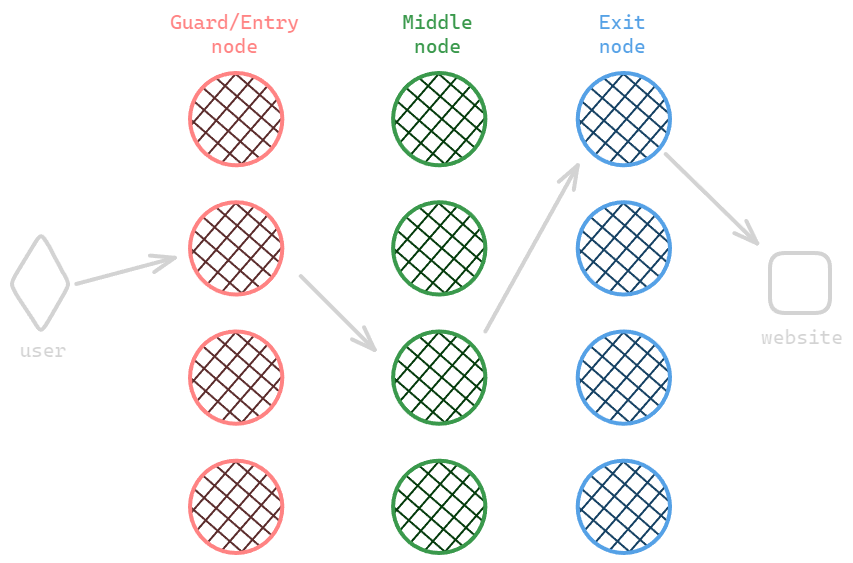
When a user is connected to the Tor network, if he’s trying to access a ‘clearnet service’, the traffic is going to pass through three nodes, if he’s trying to connect to an onion service Tor is going to use six nodes. The packet is encrypted multiple times with different keys and layers, one for each node (onion routing).
The first node is the ‘guard node’, which is a trusted entry point that is able to see our IP address, but not the service we want to connect to. Then the message it’s sent through a series of relays (Tor uses as default, one middle and one exit relay), which are other computers on the Tor network that are able to decrypt only their layer, allowing each relay only to know the IP address of the previous and next relay in the chain. The final relay decrypts the message and sends it to the destination website; the return traffic is encrypted again with the onion routing technique and sent back through the relays in the reverse order.
The usage of three relays for ‘clearnet services’ is a ‘sweet spot’ between privacy and performance. Two relays, as we said in the Apple Private Relay chapter could be risky, potentially exposing connections to the same entity. Three relays provide some deniability, however, using more than three greatly impacts client performance due to increased encryption and decryption processes.
If we’re to connect to an ‘Onion Service’ Tor is going to use six nodes: three for our anonymity and the other three to protect the onion service anonymity (hide real service IP).
Tor + VPN
Whether it is better to use Tor alone, Tor with a VPN or Tor with a bridge is an open discussion topic.
I’m going to explain the main theories of both parties, however I want to point out that unless your threat model is a very specific one (e.g. ISP/Gov), this decision is quite irrelevant.\
Some people think that the main reason you should use Tor alone is because by adding a VPN, you’re adding a potential single point of failure that can de-anonymize you, and that even if you are engaging in illegal activities that go against your government, as long as using Tor is not illegal in itself, it is safer to use it without a VPN.
Other people sustain that using a VPN before connecting to Tor is a better practice mainly because, from an ISP standpoint, commercial VPN traffic is less suspicious and would stand out less than a direct connection to Tor.
Another option to hide from your ISP that you’re using Tor is the protections provided by Tor bridges. They are regular Tor relays, but hidden from the public directory, this makes it difficult for governments or ISPs trying to block them immediately, but once the IP of the bridge has been made public they can discover connections to Tor in the past with historical traffic log analysis.
Tor de-anonymisation
Tor, and more in general, onion routing could be vulnerable to traffic analysis, which is the process of deducing information from patterns in communication, for example timing, volume, or other characteristics.
- Timing Analysis: adversaries monitoring entry and exit points of a Tor circuit might be able to identify the user by matching patterns in the timing of packets. This includes:
- Flow Correlation Attacks: Analysing the timing and size of packets to correlate traffic entering and exiting the Tor network.
- Watermarking: Injecting specific timing patterns into traffic flows. These patterns, if observed in exit traffic, could help link a user with specific activity.
- Selective Cross Correlation Attacks: attempts to filter out dummy traffic added by Tor relays to obfuscate timing analysis.
Another de-anonymisation risk is the Exit Relay Vulnerabilities: exit relays, where Tor traffic re-enters the regular internet, presenting a potential vulnerability, where a malicious exit relay operator could intercept and analyse traffic.
A recent example has been seen in 2020 where thousand of malicious servers has been added to the Tor network as “exit relays,” to identify traffic heading to cryptocurrency mixing websites and perform an SSL stripping attack, which is when traffic is downgraded from an encrypted HTTPS connection to plaintext HTTP.
De-Anonymization of the Tor Network users is a goal for law enforcement agencies that need to identify and prevent illicit activities, for that reason government agencies run Tor nodes or use exploits to track traffic back to a specific user.
Another interesting router technique is garlic routing which is mainly used in I2P and other encrypted networks.
It encapsulates messages in multiple layers of encryption and routes them through a network of nodes, like onion routing.
However, instead of simply wrapping a message in encryption layers, garlic routing bundles multiple messages, called “cloves”, together into a single encrypted structure known as “garlic”.
Each clove has its own delivery instructions, but only the final recipient can decrypt and understand its specific contents.
Additionally, garlic routing allows for the incorporation of reply blocks, enabling bidirectional communication without the need to construct entirely new routes for return messages.
This bundling increases anonymity, as it becomes more difficult to do traffic analysis.
Conclusions
It’s crucial to realise that while VPNs, Apple’s Private Relay, and Tor Network offer varying degrees of privacy protection, none guarantee complete anonymity online. Each tool has its strengths and weaknesses and the best privacy tool depends entirely on your individual needs and on your threat model.
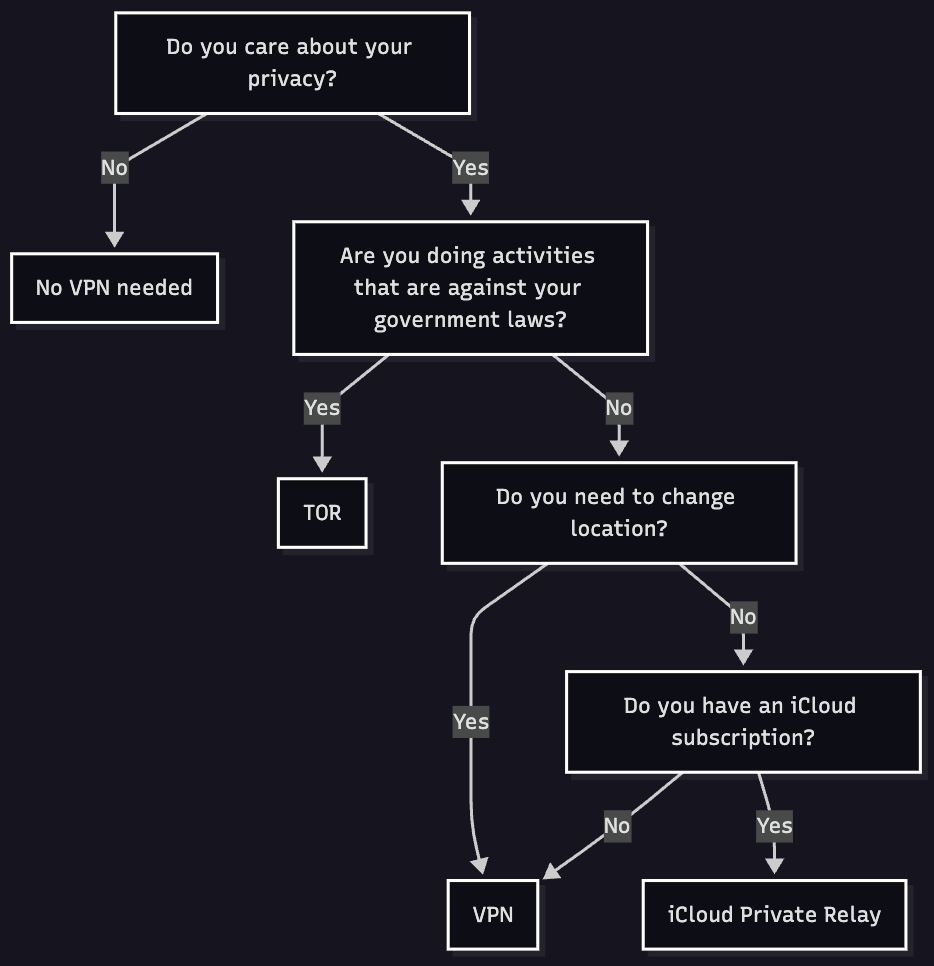
I have created this schematic and simple decision map to help decide what tool could be the best, and put together every piece of the puzzle that we discussed in this post.