Follow the money
“Follow the money” is a financial investigation technique based on tracking illicit financial flows and transaction steps to uncover the source and destination of fraud, money laundering and other organized crimes.
Financial transactions are hard evidence to destroy and are quite easy records to be accessed years after from investigators. However, criminals are constantly adapting their tactics, with funds being funnelled through a maze of international transactions and shell companies. This can make it difficult for investigators to track the flow of money, especially when it requires international cooperation between different countries with varying financial regulations.
We can usually identify the following two steps in this technique:
- Identification of suspicious transactions and collection of data
In case of money laundering suspect, it’s going to be useful the usage of an (Anti Money Laundering) AML transaction monitoring that identifies suspicious activity that may be tied to money laundering activities or other related financial crimes. Natural language processing, network analytics, and predictive analytics allows enhanced AML operations.
Usually analysts identify accounts/transactions that appear suspicious based on different factors, such as:- Amount: A big transaction or attempts at structuring large amounts of cash into multiple small transactions to avoid triggering security systems (smurfing).
- Recipient: Whether the recipient or the sender is a Politically Exposed Person (PEP), a known bad actor, or someone on a watchlist/sanction list.
- Geography: The user of either the sender or the receiver being in a high-risk country (e.g., Iran, Myanmar, Panama, Cayman Islands, and others).
- Velocity: Initiation of many transactions in a short period of time that differ from the average activity. Big gaps in transactions are also a red flag, such as a sudden three-month gap in a suspect’s credit card activity, indicating possible use of cash for routine purchases, raising questions about the cash’s origin. Political Exposed Person (PEP) additional screening is crucial for detection of corruption and money laundering for the likeliness of committing these types of crimes thanks to the positions of power and influence. This may include conducting additional due diligence on the customer’s transactions, implementing enhanced transaction monitoring, and conducting ongoing monitoring of the customer’s account.
- Analysis of the collected Financial Records and tracing the path
Analysts analyse the collected suspicious data, identifying connections between accounts and deeply studying the movement of the suspicious funds by following the financial transactions. Usually, criminals try to create layers of complexity to hide their origin, between transactions, by splitting the money into multiple ones, changing names and other information.
Blockchain and Bitcoin
Let’s make a hyper-short introduction on what Bitcoin is and how the Blockchain works. In this part we’re going to focus just on Bitcoin and not other Cryptocurrencies because, at the moment, it’s the most used and owned.
Bitcoin is a decentralised digital currency which relies on a distributed set of miners to mint coins and on a peer-to-peer network to broadcast transactions information. In order to utilize Bitcoin a consumer must first set up a Bitcoin wallet.
There are different methods to acquire Bitcoin:
- Exchange them with another user
- Purchase through an exchange
- Earn them through mining
Blockchain is essentially a distributed database shared across a network of devices. Unlike a traditional database, information is stored in blocks that are cryptographically linked together in a chronological chain. Each block contains a timestamp, reference to the previous block, and data (like transaction details). This cryptographic linkage ensures the immutability of the data: once something is recorded, it cannot be altered without altering every subsequent block.
Down below there’s an example of the Bitcoin Blockchain. If you want to understand deeper how it works, I recommend you to watch this very well-made video by 3Blue1Brown.
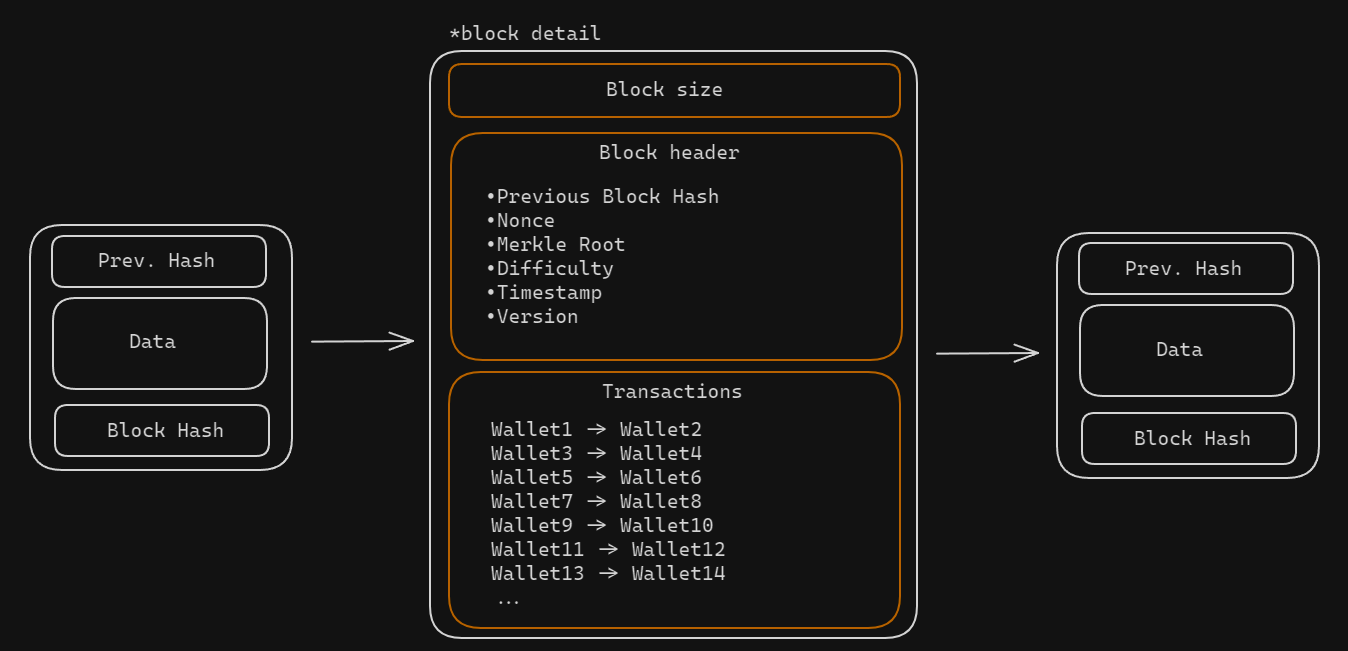
Tracking
As you can imagine, Bitcoin immutability and “pseudonymity” (we’ll discuss it later) allows potential criminal transactions to be processed in a quicker way due to the bypassing of the regulatory legal controls that we explained before.
At the same time, this transparency and immutability characteristics of the blockchain can be useful for authorities that want to verify transactions.
There are several techniques to ‘Follow the Bitcoins’:
- Haircut Taint
If you put “x” stolen bitcoin and “y” legit bitcoin in the same wallet and you spend “z” Bitcoin, then those “z” Bitcoins are “x/(x+y)%” tainted and you keep track of that. The problem of this method is that in a few hundreds blocks you end up with every block being tinted just with a little percentage. - Weighted Taint
One interesting variant that tries to avoid the dispensation problem involves the usage of a “TaintRank” assigned to each node. Combining distance-based weight, link weight, TaintRank of its predecessor nodes and the ratio of tainted transactions can help balance the taint distribution, even in long terms. - FIFO Taint
It uses the “First In First Out” mechanism, assuming that the first “x” stolen Bitcoins that are coming in the wallet are also the first “x” that are going out. By doing that the stolen bitcoins are not spread through the blockchain but remain concentrated. If this method ensures all nodes receiving funds from a tainted address are marked equally, it can definitely lead to over-tainting against some wallets. - Pattern Matching algorithm
Defined by a set of properties such as transaction time, coin amount, coin balance, total received amount, attempts to identify specific patterns or behaviours.
This method can lead to a higher confident address clustering, allowing to group addresses that are likely to be controlled by the same entity based on transaction patterns.
Usually, state agencies and big companies use services like Chainalysis or Coinfirm to perform this kind of tracing on their behalf.
Anonymity
After the tracking has been made successfully, Bitcoin deanonymization techniques can be applied.
At the beginning of the chapter I said that one of the characteristics of Bitcoin is “pseudonymity”, that’s because due to its structure these things must be considered:
- Using the same wallet repeatedly can reveal patterns and link transactions, making it possible to build profiles of user activities.
- Your wallet is public: that means everyone who has your wallet address can see how much money you have received, spent and have on your wallet.
- Most Bitcoin exchanges require personal information (ID) during registration due to AML regulations that force “Know Your Client” standards. By doing so, the exchange is linking user identities to their transactions, so law enforcements can easily identify wallet owners.
- Anyone who shared their addresses or transaction information online, even if using some offline wallet without ID verification, throughout OSINT could easily have their address associated with their real identity.
What if someone does not share this type of information and has an offline wallet?
In this case, the most common deanonymization technique involves trying to associate their wallet addresses with their IP addresses.
Bitcoin network, rely on a decentralised network of nodes for transaction verification and propagation. When a Bitcoin transaction is initiated from a wallet, the wallet must communicate with one or more nodes to broadcast the transaction to the network, primarily relying on TCP/UDP.
Both the ISP and the final node are able to see from the packet header what are the source and the destination IP addresses.
- The ISP is not able to see the content of the payload due to encryption, but it’s able to check if the destination IP is related to a Bitcoin network node.
- The final node is able to link the source IP with the wallet address. For this reason, it is expected that law enforcement agencies are hosting nodes in the network to monitor it and being able to retrieve more data.
One last similar scenario to consider is the usage of an hardware wallet (e.g. Ledger) that is plugged into a device each time a transaction is made, since the private key, needed to approve the transaction, is stored inside the hardware. Assuming that the hardware wallet manufacturer does not link in any way your personal data with the address associated with the wallet, it can be connected to different devices to create a larger pool of IP addresses and allows for greater flexibility of use.
The usage of a VPN, Tor or other tools can be useful to obfuscate the real identity by adding another security layer, but it will be interesting to see how Quantum Computing will retroactively affect the deanonymization.
To conclude, we can definitely say that:
Cash for small transactions is safer than Bitcoin.
Tools and Techniques for Crypto Privacy
Crypto Mixers (or tumbler) are services that break the connection between the sender and receiver of a transaction. Users send their Crypto to the mixer, which pools and mixes it with Crypto from other users, then sends an equivalent amount of Crypto (usually with a delay), minus a fee, to the specified recipients.
This process allows to hide the original sources, making it difficult for analysts to trace the crypto with the tracking methods that we’ve seen before.
There are mainly two types of Mixers:
- Centralised Mixers These services act as intermediaries, requiring users to trust them and pay a fee. While they typically offer faster transactions, centralised mixers come with some risks. They can track and log user information and transactions, possibly sell this data, and there is a chance they might not return your coins.
- Decentralised Mixers
These services operate on a peer-to-peer network, providing higher levels of security and anonymity since they typically do not collect user data. However, they may encounter challenges such as slower transaction speeds and recognizable patterns that could potentially be flagged.
The most common protocol is known as CoinJoin, where multiple actors sign a smart contract to mix their coins together and create multiple outputs with the same number of coins, making external tracking difficult. Unlike centralised mixers, users maintain the custody of their coins during all this process.
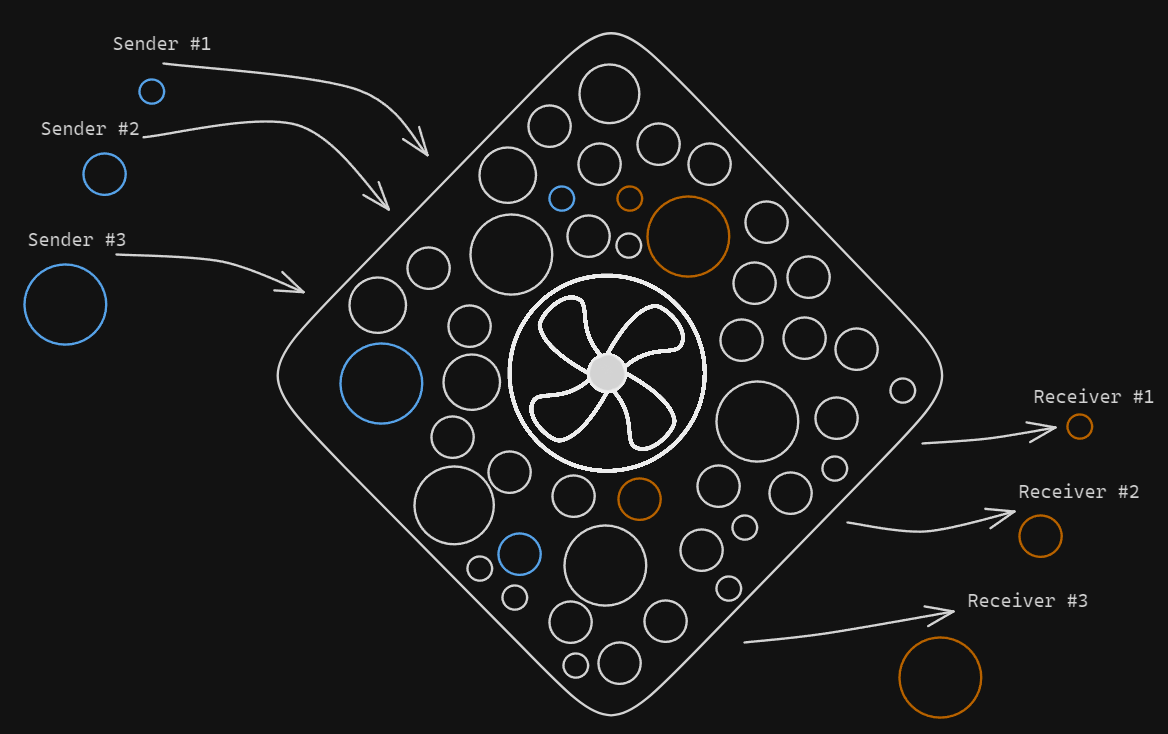
PeelChain is a layering method used to gradually transfer cryptocurrency from one address to another through a series of smaller transactions. Each transaction sends a small portion of the original amount to a new address while transferring the remaining balance to yet another new address, creating a numerous chain of transactions.
This process attempts to obfuscate the origin of the funds by creating a complex transaction trail, but it is less secure if not used in conjunction with a Crypto Mixer.
ChainHopping is the process of rapidly moving between different cryptocurrencies, usually with the usage of Cross Chain Bridges, to create a complex transaction history. With this method “privacy coins” like Monero (we’ll talk about it later) are commonly used; without the usage of these types of coins, analysts can easily trace a user, even throughout different Blockchains.
DarkWallet was a Privacy-oriented wallet project that included some of the tools that we just saw such as a Stealth Address and an integrated Mixer. Although this Project was never finished, it served as a pioneer for other similar projects and coins with anonymity benefits.
One last tool that worth mentioning are the Bitcoin ATMs which offer a way to buy and sell Bitcoin anonymously, because some of them do not require any ID, but usually they charge high fees and have daily limits.
Monero and similar
Monero is a cryptocurrency based on the Open Source CryptoNote protocol, with a specific attention towards privacy, anonymity and fungibility.
There are three main elements that allow these properties:
- Ring Signature allows to ensure the anonymity of transactions by combining the sender’s key with a set of decoy keys from past transactions on the blockchain, creating a “ring” of possible signers where all members are equal and valid, but computationally infeasible to determine which member produced the signature.
- Confidential Transactions ensures that only the sender and receiver know the transaction amount. RingCT converts the transaction into a cryptographic construction called ‘commitment’ allows a value to be hidden while enabling others to verify that it falls within a certain range. For a transaction to be valid, the sum of the input commitments must equal the sum of the output commitments plus the transaction fee commitment. This ensures no extra money is created or destroyed in the transaction.
- Stealth Addresses generate unique, one-time addresses for each transaction. This ensures that each transaction has a distinct address that cannot be linked to any other transaction or the recipient’s primary address.
The usage of these technologies such as Ring Confidential Transactions result in larger transaction sizes, which contribute to a rapid growth of the blockchain (Blockchain Bloat) leading to potential issue such as more challenging for nodes to store and verify the entire blockchain, potentially leading to a decrease in decentralisation and higher transaction fees.
During the last year, Monero has been delisted by the mains Exchange platforms such as Binance, Kraken and others due to concerns over its privacy features, which make it difficult for authorities to trace transactions and comply AML and KYC regulations.
There are also other famous privacy-driven alternative coins such as Dash and ZCash, but neither of these cryptocurrencies are as private as Monero by default. This is likely a strategic decision to prevent delisting from major exchanges.